qmail variants
s/qmail
qmail-ldap, by André Oppermann (LinkedIn, Xing)
Life With qmail-ldap
freshports.org
qmail
qmail-tls: Secure, reliable, and fast MTA for UNIX systems with TLS support
Repository
https://cgit.freebsd.org/ports/tree/mail/qmail?h=release/12.2.0
FreeBSD 10.2
| ZHAW -> tE-Clan Server ==> works |
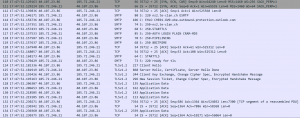 |
| tE-Clan Server -> ZHAW ==> DOESN’T work!! |
 |
$ pkg info netqmail-tls
netqmail-tls-1.06.20110119_1
Name : netqmail-tls
Version : 1.06.20110119_1
Installed on : Fri Dec 11 10:59:23 2015 CET
Origin : mail/qmail-tls
Architecture : freebsd:10:x86:64
Prefix : /var/qmail
Categories : mail
Licenses :
Maintainer : erdgeist@erdgeist.org
WWW : http://inoa.net/qmail-tls/
Comment : Secure, reliable, and fast MTA for UNIX systems with TLS support
Options :
BIG_CONCURRENCY_PATCH: off
BIG_TODO_PATCH : on
BLOCKEXEC_PATCH: on
DISCBOUNCES_PATCH: off
DNS_CNAME : on
DOCS : on
EXTTODO_PATCH : off
LOCALTIME_PATCH: off
MAILDIRQUOTA_PATCH: off
OUTGOINGIP_PATCH: on
QEXTRA : off
QMTPC_PATCH : off
RCDLINK : off
SMTP_AUTH_PATCH: off
SPF_PATCH : off
TLS_DEBUG : off
Annotations :
Flat size : 1.06MiB
Description :
What is is: [excerpt taken from tls patch]
Frederik Vermeulen <qmail-tls at inoa.net> 20021228
http://inoa.net/qmail/qmail-1.03-tls.patch
This patch implements RFC2487 in qmail. This means you can
get SSL or TLS encrypted and authenticated SMTP between
the MTAs and between MTA and an MUA like Netscape4.5 TM.
The code is considered experimental.
WWW: http://inoa.net/qmail-tls/
# tail /var/log/qmail/current | tai64nlocal 2021-07-09 16:13:31.006863500 status: local 1/10 remote 0/20 2021-07-09 16:13:31.020170500 delivery 47043: success: did_0+0+1/ 2021-07-09 16:13:31.020288500 status: local 0/10 remote 0/20 2021-07-09 16:13:31.020361500 end msg 963489 2021-07-09 16:37:34.013898500 new msg 963470 2021-07-09 16:37:34.013922500 info msg 963470: bytes 2686 from <XXX> qp 17787 uid 89 2021-07-09 16:37:34.398681500 starting delivery 47044: msg 963470 to remote XXX@hotmail.com 2021-07-09 16:37:34.398686500 status: local 0/10 remote 1/20 2021-07-09 16:37:35.411841500 delivery 47044: deferral: TLS_connect_failed;_connected_to_104.47.73.161./ 2021-07-09 16:37:35.411846500 status: local 0/10 remote 0/20 2021-07-09 16:44:15.431323500 starting delivery 47045: msg 963470 to remote XXX@hotmail.com 2021-07-09 16:44:15.431328500 status: local 0/10 remote 1/20 2021-07-09 16:44:15.841424500 delivery 47045: deferral: TLS_connect_failed;_connected_to_104.47.17.161./ 2021-07-09 16:44:15.841460500 status: local 0/10 remote 0/20 2021-07-09 17:04:15.098384500 starting delivery 47047: msg 963470 to remote XXX@hotmail.com 2021-07-09 17:04:15.098390500 status: local 0/10 remote 1/20 2021-07-09 17:04:15.289859500 delivery 47047: deferral: TLS_connect_failed;_connected_to_104.47.10.33./ 2021-07-09 17:04:15.289889500 status: local 0/10 remote 0/20
[root@ns2 /usr/ports/mail/qmail-tls]# make install
You may use the following build options:
WITH_BIG_CONCURRENCY_PATCH_CONCURRENCY_LIMIT=NUMBER
(default NUMBER=)
set this to a value reasonable for
your system if you use the patch
===> netqmail-tls-1.06.20110119_1 has known vulnerabilities:
netqmail-tls-1.06.20110119_1 is vulnerable:
qmail -- 64 bit integer overflows with possible remote code execution on large SMTP requests
CVE: CVE-2005-1515
CVE: CVE-2005-1514
CVE: CVE-2005-1513
WWW: https://vuxml.FreeBSD.org/freebsd/b495af21-9e10-11ea-9e83-0cc47ac16c9d.html
1 problem(s) in the installed packages found.
=> Please update your ports tree and try again.
=> Note: Vulnerable ports are marked as such even if there is no update available.
=> If you wish to ignore this vulnerability rebuild with 'make DISABLE_VULNERABILITIES=yes'
*** Error code 1
Stop.
make[1]: stopped in /usr/ports/mail/qmail-tls
*** Error code 1
Stop.
make: stopped in /usr/ports/mail/qmail-tls
.if defined(SLAVE_LDAP)
PATCH_SITES+= http://www.nrg4u.com/qmail/:ldap
PATCHFILES+= qmail-ldap-1.03-${LDAP_PATCH_DATE}.patch.gz:ldap
.elif defined(SLAVE_MYSQL)
PATCH_SITES+= http://iain.cx/unix/qmail/download/:mysql
PATCHFILES+= netqmail-mysql-${MYSQL_PATCH_VERSION}.patch:mysql
.elif defined(SLAVE_TLS)
PATCH_SITES+= http://inoa.net/qmail-tls/:tls
TLS_PATCH_NAME= ${QMAIL_PORTNAME}-${QMAIL_VERSION}-tls-${TLS_PATCH_DATE}.patch
PATCHFILES+= ${TLS_PATCH_NAME}:tls
.endif
PORTNAME= qmail
PORTVERSION= ${QMAIL_VERSION}.${TLS_PATCH_DATE}
PKGNAMESUFFIX= -tls
SLAVE_TLS= yes
TLS_PATCH_DATE= 20110119
# where pkg_add records its dirty deeds.
PKG_DBDIR?= /var/db/pkg
AUDITFILE?= ${PKG_DBDIR}/vuln.xml
check-vulnerable:
.if !defined(DISABLE_VULNERABILITIES) && !defined(PACKAGE_BUILDING)
[...]
${ECHO_MSG} "===> ${PKGNAME} has known vulnerabilities:"; \
${ECHO_MSG} "$$vlist"; \
${ECHO_MSG} "=> Please update your ports tree and try again."; \
${ECHO_MSG} "=> Note: Vulnerable ports are marked as such even if there is no update available."; \
${ECHO_MSG} "=> If you wish to ignore this vulnerability rebuild with 'make DISABLE_VULNERABILITIES=yes'"; \
<topic>qmail -- 64 bit integer overflows with possible remote code execution on large SMTP requests</topic>
<name>netqmail</name>
<name>netqmail-tls</name>
<name>netqmail-mysql</name>
Chapter 4. Slow Porting: 4.4. Patching
- […]
- […]
- The patch target is run. First, any patches defined in PATCHFILES are applied. Second, if any patch files named patch-* are found in PATCHDIR (defaults to the files subdirectory), they are applied at this time in alphabetical order.
- […]
===> netqmail-tls-1.06.20200107_4 depends on file: /usr/local/sbin/pkg - found => qmail-smtpd-auth-0.31.tar.gz doesn't seem to exist in /usr/ports/distfiles/qmail. => Attempting to fetch http://tomclegg.net/qmail/qmail-smtpd-auth-0.31.tar.gz qmail-smtpd-auth-0.31.tar.gz 100% of 8798 B 27 MBps 00m00s => qmail-smtpd-auth-close3.patch doesn't seem to exist in /usr/ports/distfiles/qmail. => Attempting to fetch http://tomclegg.net/qmail/qmail-smtpd-auth-close3.patch qmail-smtpd-auth-close3.patch 100% of 520 B 2791 kBps 00m00s => auth.patch.diff-tls-20110119 doesn't seem to exist in /usr/ports/distfiles/qmail. => Attempting to fetch http://tomclegg.net/qmail/auth.patch.diff-tls-20110119 fetch: http://tomclegg.net/qmail/auth.patch.diff-tls-20110119: Not Found => Attempting to fetch http://distcache.FreeBSD.org/local-distfiles/bdrewery/qmail/auth.patch.diff-tls-20110119 auth.patch.diff-tls-20110119 100% of 3170 B 18 MBps 00m00s => netqmail-1.06-tls-20200107.patch doesn't seem to exist in /usr/ports/distfiles/qmail. => Attempting to fetch http://inoa.net/qmail-tls/netqmail-1.06-tls-20200107.patch netqmail-1.06-tls-20200107.patch 100% of 50 kB 3567 kBps 00m00s ===> Fetching all distfiles required by netqmail-tls-1.06.20200107_4 for building ===> Extracting for netqmail-tls-1.06.20200107_4 => SHA256 Checksum OK for qmail/netqmail-1.06.tar.gz. => SHA256 Checksum OK for qmail/qmail-smtpd-auth-0.31.tar.gz. => SHA256 Checksum OK for qmail/qmail-smtpd-auth-close3.patch. => SHA256 Checksum OK for qmail/auth.patch.diff-tls-20110119. => SHA256 Checksum OK for qmail/qmail-103.patch. => No SHA256 checksum recorded for qmail/netqmail-1.06-tls-20200107.patch. => No suitable checksum found for qmail/netqmail-1.06-tls-20200107.patch. => SHA256 Checksum OK for qmail/qmail-block-executables.patch. => SHA256 Checksum OK for qmail/big-todo.103.patch. => SHA256 Checksum OK for qmail/outgoingip.patch. *** Error code 1 Stop. make[1]: stopped in /usr/ports/mail/qmail-tls *** Error code 1 Stop. make: stopped in /usr/ports/mail/qmail-tls
# cd /usr/ports/mail/qmail-tls # make makesum ===> Found saved configuration for netqmail-tls-1.06.20200107_4 ===> netqmail-tls-1.06.20200107_4 depends on file: /usr/local/sbin/pkg - found ===> Fetching all distfiles required by netqmail-tls-1.06.20200107_4 for building # make ===> Found saved configuration for netqmail-tls-1.06.20200107_4 ===> netqmail-tls-1.06.20200107_4 depends on file: /usr/local/sbin/pkg - found ===> Fetching all distfiles required by netqmail-tls-1.06.20200107_4 for building ===> Extracting for netqmail-tls-1.06.20200107_4 => SHA256 Checksum OK for qmail/netqmail-1.06.tar.gz. => SHA256 Checksum OK for qmail/qmail-smtpd-auth-0.31.tar.gz. => SHA256 Checksum OK for qmail/qmail-smtpd-auth-close3.patch. => SHA256 Checksum OK for qmail/auth.patch.diff-tls-20110119. => SHA256 Checksum OK for qmail/qmail-103.patch. => SHA256 Checksum OK for qmail/netqmail-1.06-tls-20200107.patch. => SHA256 Checksum OK for qmail/qmail-block-executables.patch. => SHA256 Checksum OK for qmail/big-todo.103.patch. => SHA256 Checksum OK for qmail/outgoingip.patch. ===> Patching for netqmail-tls-1.06.20200107_4 ===> Applying distribution patches for netqmail-tls-1.06.20200107_4 ===> Applying extra patch /usr/ports/mail/qmail-tls/../qmail/files/extra-patch-amd64 ===> Applying extra patch /usr/ports/mail/qmail-tls/../qmail/files/extra-patch-utmpx ===> Applying extra patch /usr/ports/mail/qmail-tls/../qmail/files/extra-patch-dns-cname ===> Applying FreeBSD patches for netqmail-tls-1.06.20200107_4 [...] # ps auxd - /usr/local/bin/svscan /var/service |-- supervise pop3d | `-- /usr/local/bin/tcpserver -vDHR -l0 -c200 -xtcp.cdb -- 0 110 /var/qmail/bin/qmail-popup ns2.te-clan.ch /usr/local/vpopmail/bin/vchkpw /var/qmail/bin/qmail-pop3d Maildir |-- supervise log | `-- multilog t ./main |-- supervise smtpd | `-- /usr/local/bin/tcpserver -vDUHR -lns2.te-clan.ch -c200 -xtcp.cdb -- 0 25 /usr/local/bin/greylite /var/qmail/bin/qmail-smtpd /usr/local/vpopmail/bin/vchkpw /bin/true | |-- /usr/local/bin/greylite /var/qmail/bin/qmail-smtpd /usr/local/vpopmail/bin/vchkpw /bin/true | | `-- /var/qmail/bin/qmail-smtpd /usr/local/vpopmail/bin/vchkpw /bin/true | |-- /usr/local/bin/greylite /var/qmail/bin/qmail-smtpd /usr/local/vpopmail/bin/vchkpw /bin/true | | `-- /var/qmail/bin/qmail-smtpd /usr/local/vpopmail/bin/vchkpw /bin/true | |-- /usr/local/bin/greylite /var/qmail/bin/qmail-smtpd /usr/local/vpopmail/bin/vchkpw /bin/true | | `-- /var/qmail/bin/qmail-smtpd /usr/local/vpopmail/bin/vchkpw /bin/true | |-- /usr/local/bin/greylite /var/qmail/bin/qmail-smtpd /usr/local/vpopmail/bin/vchkpw /bin/true | | `-- /var/qmail/bin/qmail-smtpd /usr/local/vpopmail/bin/vchkpw /bin/true | `-- /usr/local/bin/greylite /var/qmail/bin/qmail-smtpd /usr/local/vpopmail/bin/vchkpw /bin/true | `-- /var/qmail/bin/qmail-smtpd /usr/local/vpopmail/bin/vchkpw /bin/true |-- supervise log | `-- multilog t ./main |-- supervise qmail | `-- qmail-send | |-- /usr/local/bin/multilog t /var/log/qmail qmaill | |-- qmail-lspawn ./Maildir/ | |-- qmail-rspawn | `-- qmail-clean `-- supervise log `-- multilog t ./main # find work -name qmail-remote work/netqmail-1.06/qmail-remote work/stage/var/qmail/bin/qmail-remote # /usr/local/etc/rc.d/svscan stop Stopping svscan. Waiting for PIDS: 731. # cp /usr/ports/mail/qmail-tls/work/stage/var/qmail/bin/qmail-remote /var/qmail/bin/qmail-remote # /usr/local/etc/rc.d/svscan start
qmail mit TLS
smtp-auth + qmail-tls + forcetls patch for qmail, May 8, 2020
Patching qmail, June 19, 2021
Installing and configuring vpopmail, April 18, 2021
Installing Dovecot and sieve on a vpopmail + qmail server, June 20, 2021
Was ist TLS
SMTP and Transport Layer Security (TLS) [Tutorial]
Microsoft unterstützt TLS 1.0 nicht mehr!
TLS connect failed
SSL/TLS connection issue troubleshooting test tools
Can’t establish a TLS connection to a remote mail server in Exchange Online or Exchange Server
TLS negotiating failed
Office 365 to enforce TLS 1.2 per October 15, 2020
Checking security protocols and ciphers on your Exchange servers
Rehash: How to Fix the SSL/TLS Handshake Failed Error
SSL/TLS connection issue troubleshooting guide
SSL/TLS connection issue troubleshooting test tools
SMTP MTA STS
SMTP MTA STS (Strict Transport Security)
MTA-STS gestaltet Mail-Versand und -Empfang sicherer
STARTTLS: MTA-STS
OpenSSL
E-Mail-Verschlüsselung austesten
When was TLS 1.2 support added to OpenSSL?
# openssl version OpenSSL 1.0.1p-freebsd 9 Jul 2015
From ns3.te-clan.ch
$ openssl s_client -host mail.te-clan.ch -port 25 -starttls smtp
CONNECTED(00000003)
ehlo test
depth=0 C = CH, ST = ZH, L = Winterthur, O = tE-clan Server, CN = Andreas Bachmann, emailAddress = bachi@te-clan.ch
verify error:num=18:self signed certificate
verify return:1
depth=0 C = CH, ST = ZH, L = Winterthur, O = tE-clan Server, CN = Andreas Bachmann, emailAddress = bachi@te-clan.ch
verify return:1
---
Certificate chain
0 s:C = CH, ST = ZH, L = Winterthur, O = tE-clan Server, CN = Andreas Bachmann, emailAddress = bachi@te-clan.ch
i:C = CH, ST = ZH, L = Winterthur, O = tE-clan Server, CN = Andreas Bachmann, emailAddress = bachi@te-clan.ch
---
Server certificate
-----BEGIN CERTIFICATE-----
[...]
-----END CERTIFICATE-----
subject=C = CH, ST = ZH, L = Winterthur, O = tE-clan Server, CN = Andreas Bachmann, emailAddress = bachi@te-clan.ch
issuer=C = CH, ST = ZH, L = Winterthur, O = tE-clan Server, CN = Andreas Bachmann, emailAddress = bachi@te-clan.ch
---
No client certificate CA names sent
Peer signing digest: SHA256
Peer signature type: RSA
Server Temp Key: DH, 1024 bits
---
SSL handshake has read 1600 bytes and written 542 bytes
Verification error: self signed certificate
---
New, TLSv1.2, Cipher is DHE-RSA-AES256-GCM-SHA384
Server public key is 1024 bit
Secure Renegotiation IS supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
SSL-Session:
Protocol : TLSv1.2
Cipher : DHE-RSA-AES256-GCM-SHA384
Session-ID: [...]
Session-ID-ctx:
Master-Key: [...]
PSK identity: None
PSK identity hint: None
SRP username: None
TLS session ticket lifetime hint: 300 (seconds)
TLS session ticket:
0000 - 0b f4 09 ef 02 07 df bc-b9 fa bd d0 f6 21 af 69 .............!.i
0010 - [...]
00a0 - ff 5d 6f 73 8d 1b 75 59-bf dd 9b a6 d8 b2 01 71 .]os..uY.......q
Start Time: 1625840075
Timeout : 7200 (sec)
Verify return code: 18 (self signed certificate)
Extended master secret: no
---
250 8BITMIME
250-ns2.te-clan.ch250-AUTH LOGIN PLAIN CRAM-MD5
250-PIPELINING
250 8BITMIME
read:errno=0
From ns3.te-clan.ch
$ openssl s_client -host 104.47.74.33 -port 25 -starttls smtp
CONNECTED(00000003)
depth=2 C = US, O = DigiCert Inc, OU = www.digicert.com, CN = DigiCert Global Root CA
verify return:1
depth=1 C = US, O = DigiCert Inc, CN = DigiCert Cloud Services CA-1
verify return:1
depth=0 C = US, ST = Washington, L = Redmond, O = Microsoft Corporation, CN = mail.protection.outlook.com
verify return:1
---
Certificate chain
0 s:C = US, ST = Washington, L = Redmond, O = Microsoft Corporation, CN = mail.protection.outlook.com
i:C = US, O = DigiCert Inc, CN = DigiCert Cloud Services CA-1
1 s:C = US, O = DigiCert Inc, CN = DigiCert Cloud Services CA-1
i:C = US, O = DigiCert Inc, OU = www.digicert.com, CN = DigiCert Global Root CA
---
Server certificate
-----BEGIN CERTIFICATE-----
[...]
-----END CERTIFICATE-----
subject=C = US, ST = Washington, L = Redmond, O = Microsoft Corporation, CN = mail.protection.outlook.com
issuer=C = US, O = DigiCert Inc, CN = DigiCert Cloud Services CA-1
---
No client certificate CA names sent
Client Certificate Types: RSA sign, DSA sign, ECDSA sign
Requested Signature Algorithms: RSA+SHA256:RSA+SHA384:RSA+SHA1:ECDSA+SHA256:ECDSA+SHA384:ECDSA+SHA1:DSA+SHA1:RSA+SHA512:ECDSA+SHA512
Shared Requested Signature Algorithms: RSA+SHA256:RSA+SHA384:RSA+SHA1:ECDSA+SHA256:ECDSA+SHA384:ECDSA+SHA1:DSA+SHA1:RSA+SHA512:ECDSA+SHA512
Peer signing digest: SHA256
Peer signature type: RSA
Server Temp Key: ECDH, P-384, 384 bits
---
SSL handshake has read 3852 bytes and written 519 bytes
Verification: OK
---
New, TLSv1.2, Cipher is ECDHE-RSA-AES256-GCM-SHA384
Server public key is 2048 bit
Secure Renegotiation IS supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
SSL-Session:
Protocol : TLSv1.2
Cipher : ECDHE-RSA-AES256-GCM-SHA384
Session-ID: [...]
Session-ID-ctx:
Master-Key: [...]
PSK identity: None
PSK identity hint: None
SRP username: None
Start Time: 1625840474
Timeout : 7200 (sec)
Verify return code: 0 (ok)
Extended master secret: yes
---
250 SMTPUTF8
From ns2.te-clan.ch
$ openssl s_client -host 104.47.74.33 -port 25 -starttls smtp
CONNECTED(00000003)
depth=2 C = US, O = DigiCert Inc, OU = www.digicert.com, CN = DigiCert Global Root CA
verify return:1
depth=1 C = US, O = DigiCert Inc, CN = DigiCert Cloud Services CA-1
verify return:1
depth=0 C = US, ST = Washington, L = Redmond, O = Microsoft Corporation, CN = mail.protection.outlook.com
verify return:1
---
Certificate chain
0 s:/C=US/ST=Washington/L=Redmond/O=Microsoft Corporation/CN=mail.protection.outlook.com
i:/C=US/O=DigiCert Inc/CN=DigiCert Cloud Services CA-1
1 s:/C=US/O=DigiCert Inc/CN=DigiCert Cloud Services CA-1
i:/C=US/O=DigiCert Inc/OU=www.digicert.com/CN=DigiCert Global Root CA
---
Server certificate
-----BEGIN CERTIFICATE-----
[...]
-----END CERTIFICATE-----
subject=/C=US/ST=Washington/L=Redmond/O=Microsoft Corporation/CN=mail.protection.outlook.com
issuer=/C=US/O=DigiCert Inc/CN=DigiCert Cloud Services CA-1
---
No client certificate CA names sent
---
SSL handshake has read 3847 bytes and written 502 bytes
---
New, TLSv1/SSLv3, Cipher is ECDHE-RSA-AES256-GCM-SHA384
Server public key is 2048 bit
Secure Renegotiation IS supported
Compression: NONE
Expansion: NONE
SSL-Session:
Protocol : TLSv1.2
Cipher : ECDHE-RSA-AES256-GCM-SHA384
Session-ID: [...]
Session-ID-ctx:
Master-Key: [...]
Key-Arg : None
PSK identity: None
PSK identity hint: None
SRP username: None
Start Time: 1625840680
Timeout : 300 (sec)
Verify return code: 0 (ok)
---
250 SMTPUTF8
OpenSSL Cookbook
Testing Protocols that Upgrade to TLS
When used with HTTP, TLS wraps the entire plain-text communication channel to form HTTPS. Some other protocols start off as plaintext, but then they upgrade to encryption. If you want to test such a protocol, you’ll have to tell OpenSSL which protocol it is so that it can upgrade on your behalf. Provide the protocol information using the -starttls switch. For example:
$ openssl s_client -connect gmail-smtp-in.l.google.com:25 -starttls smtp
At the time of writing, the supported protocols in recent OpenSSL releases are smtp, pop3, imap, ftp, xmpp, xmpp-server, irc, postgres, mysql, lmtp, nntp, sieve, and ldap. There is less choice with OpenSSL 1.0.2g: smtp, pop3, imap, ftp, and xmpp.
Some protocols require the client to provide their names. For example, for SMTP, OpenSSL will use mail.example.com by default, but you can specify the correct value with the -name switch. If you’re testing XMPP, you may need to specify the correct server name; you can do this with the -xmpphost switch.
s/qmail
Linked: Erwin Hoffmann
github.com/wavemechanics/sqmail-port
Installing s/qmail
FreeBSD Port: qmail-spamcontrol-1.03.2731_2
IndiMail
IndiMail is a Secure, Reliable, Efficient Messaging Platform which provides you everything needed in a modern messaging server – ESMTP, IMAP, POP3, QMTP, QMQP and many other features. IndiMail gives you speeds that are faster than most MTAs. The flexibility provided by IndiMail’s authentication methods allow any IMAP/POP3 server to be used with IndiMail. IndiMail is built for speed and flexibility. You can download the source or use the binary RPM generated by openSUSE Build Service.
IndiMail
IndiMail
github.com/mbhangui/indimail-mta
sslscan
github.com/rbsec/sslscan
sslscan Fast SSL port scanner
C:\Users\andreas\Downloads\sslscan-win-2.0.10>sslscan.exe --starttls-smtp mail.xyz.abc:25 Version: 2.0.10 Windows 64-bit (Mingw) OpenSSL 1.1.1e-dev xx XXX xxxx Connected to x.x.x.x Testing SSL server mail.xyz.abc on port 25 using SNI name mail.xyz.abc SSL/TLS Protocols: SSLv2 enabled SSLv3 disabled TLSv1.0 enabled TLSv1.1 enabled TLSv1.2 enabled TLSv1.3 disabled TLS Fallback SCSV: Connection failed - unable to determine TLS Fallback SCSV support TLS renegotiation: Session renegotiation not supported TLS Compression: Compression disabled Heartbleed: TLSv1.2 not vulnerable to heartbleed TLSv1.1 not vulnerable to heartbleed TLSv1.0 not vulnerable to heartbleed Supported Server Cipher(s): Preferred TLSv1.2 56 bits TLS_RSA_WITH_DES_CBC_SHA Preferred TLSv1.1 56 bits TLS_RSA_WITH_DES_CBC_SHA Preferred TLSv1.1 56 bits TLS_DHE_RSA_WITH_DES_CBC_SHA Preferred TLSv1.0 256 bits DHE-RSA-AES256-SHA DHE 1024 bits Accepted TLSv1.0 56 bits TLS_RSA_WITH_DES_CBC_SHA SSL Certificate: Signature Algorithm: sha1WithRSAEncryption RSA Key Strength: 1024 Subject: Andreas Bachmann Issuer: Andreas Bachmann Not valid before: Apr 22 11:27:56 2019 GMT Not valid after: Apr 20 11:27:56 2024 GMT
FreeBSD Ports: qmail-tls
# make clean # make rmconfig # make patch [...] ===> Patching for netqmail-tls-1.06.20200107_4 ===> Applying distribution patches for netqmail-tls-1.06.20200107_4 ===> Applying extra patch /usr/ports/mail/qmail-tls/../qmail/files/extra-patch-amd64 ===> Applying extra patch /usr/ports/mail/qmail-tls/../qmail/files/extra-patch-utmpx ===> Applying extra patch /usr/ports/mail/qmail-tls/../qmail/files/extra-patch-dns-cname ===> Applying FreeBSD patches for netqmail-tls-1.06.20200107_4 from /usr/ports/mail/qmail-tls/../qmail/files Hmm... Looks like a unified diff to me... The text leading up to this was: -------------------------- |--- auth.patch.orig 2002-05-10 00:41:20.000000000 -0500 |+++ auth.patch 2014-06-24 14:30:00.122166435 -0500 -------------------------- Patching file auth.patch using Plan A... Hunk #1 succeeded at 14. Hunk #2 succeeded at 176. done Hmm... Looks like a new-style context diff to me... The text leading up to this was: -------------------------- |*** Makefile.orig Mon Jun 15 05:53:16 1998 |--- Makefile Fri May 10 00:31:38 2002 -------------------------- Patching file Makefile using Plan A... Hunk #1 succeeded at 125 (offset -11 lines). Hunk #2 succeeded at 1545 (offset 4 lines). Hunk #3 succeeded at 1548 (offset -9 lines). Hmm... The next patch looks like a new-style context diff to me... The text leading up to this was: -------------------------- | | |*** TARGETS.orig Mon Jun 15 05:53:16 1998 |--- TARGETS Fri May 10 00:31:38 2002 -------------------------- Patching file TARGETS using Plan A... Hunk #1 succeeded at 252 (offset 2 lines). Hmm... The next patch looks like a new-style context diff to me... The text leading up to this was: -------------------------- | | |*** qmail-smtpd.8.orig Mon Jun 15 05:53:16 1998 |--- qmail-smtpd.8 Fri May 10 00:31:38 2002 -------------------------- Patching file qmail-smtpd.8 using Plan A... Hunk #1 succeeded at 3. Hunk #2 succeeded at 37 (offset 9 lines). Hunk #3 succeeded at 256 (offset 52 lines). Hmm... The next patch looks like a new-style context diff to me... The text leading up to this was: -------------------------- | | |*** qmail-smtpd.c.orig Mon Jun 15 05:53:16 1998 |--- qmail-smtpd.c Fri May 10 00:33:35 2002 -------------------------- Patching file qmail-smtpd.c using Plan A... Hunk #1 succeeded at 23. Hunk #2 succeeded at 89 with fuzz 1 (offset 27 lines). Hunk #3 succeeded at 254 with fuzz 2 (offset -23 lines). Hunk #4 succeeded at 852 with fuzz 2 (offset 438 lines). No such line 845 in input file, ignoring Hunk #5 succeeded at 624 (offset -20 lines). done Hmm... Looks like a unified diff to me... The text leading up to this was: -------------------------- |--- qmail-smtpd.c.orig Sat Jan 18 09:13:50 2003 |+++ qmail-smtpd.c Sat Jan 18 19:51:09 2003 -------------------------- Patching file qmail-smtpd.c using Plan A... Hunk #1 succeeded at 883 (offset 424 lines). done
# make [...] ===> Staging for netqmail-tls-1.06.20200107_4 ===> Generating temporary packing list ===> Creating groups. ===> Creating users install -s -m 555 /usr/ports/mail/qmail-tls/work/netqmail-1.06/dnsfq /usr/ports/mail/qmail-tls/work/stage/var/qmail/configure install -s -m 555 /usr/ports/mail/qmail-tls/work/netqmail-1.06/hostname /usr/ports/mail/qmail-tls/work/stage/var/qmail/configure install -s -m 555 /usr/ports/mail/qmail-tls/work/netqmail-1.06/dnsip /usr/ports/mail/qmail-tls/work/stage/var/qmail/configure install -s -m 555 /usr/ports/mail/qmail-tls/work/netqmail-1.06/ipmeprint /usr/ports/mail/qmail-tls/work/stage/var/qmail/configure install -s -m 555 /usr/ports/mail/qmail-tls/work/netqmail-1.06/dnsptr /usr/ports/mail/qmail-tls/work/stage/var/qmail/configure install -s -m 555 /usr/ports/mail/qmail-tls/work/netqmail-1.06/install.nostage /usr/ports/mail/qmail-tls/work/stage/var/qmail/configure/install install -m 555 /usr/ports/mail/qmail-tls/work/netqmail-1.06/config /usr/ports/mail/qmail-tls/work/stage/var/qmail/configure install -m 555 /usr/ports/mail/qmail-tls/work/netqmail-1.06/config-fast /usr/ports/mail/qmail-tls/work/stage/var/qmail/configure install -m 555 /usr/ports/mail/qmail-tls/work/home /usr/ports/mail/qmail-tls/work/stage/var/qmail/boot install -m 555 /usr/ports/mail/qmail-tls/work/home+df /usr/ports/mail/qmail-tls/work/stage/var/qmail/boot install -m 555 /usr/ports/mail/qmail-tls/work/proc /usr/ports/mail/qmail-tls/work/stage/var/qmail/boot install -m 555 /usr/ports/mail/qmail-tls/work/proc+df /usr/ports/mail/qmail-tls/work/stage/var/qmail/boot install -m 555 /usr/ports/mail/qmail-tls/work/binm1 /usr/ports/mail/qmail-tls/work/stage/var/qmail/boot install -m 555 /usr/ports/mail/qmail-tls/work/binm1+df /usr/ports/mail/qmail-tls/work/stage/var/qmail/boot install -m 555 /usr/ports/mail/qmail-tls/work/binm2 /usr/ports/mail/qmail-tls/work/stage/var/qmail/boot install -m 555 /usr/ports/mail/qmail-tls/work/binm2+df /usr/ports/mail/qmail-tls/work/stage/var/qmail/boot install -m 555 /usr/ports/mail/qmail-tls/work/binm3 /usr/ports/mail/qmail-tls/work/stage/var/qmail/boot install -m 555 /usr/ports/mail/qmail-tls/work/binm3+df /usr/ports/mail/qmail-tls/work/stage/var/qmail/boot install -m 555 /usr/ports/mail/qmail-tls/work/maildir /usr/ports/mail/qmail-tls/work/stage/var/qmail/boot install -m 555 /usr/ports/mail/qmail-tls/work/qmailsmtpd /usr/ports/mail/qmail-tls/work/stage/var/qmail/boot install -m 555 /usr/ports/mail/qmail-tls/work/qmailsend /usr/ports/mail/qmail-tls/work/stage/var/qmail/boot install -m 444 /usr/ports/mail/qmail-tls/work/netqmail-1.06/forward.1 /usr/ports/mail/qmail-tls/work/stage/var/qmail/man/man1 install -m 444 /usr/ports/mail/qmail-tls/work/netqmail-1.06/condredirect.1 /usr/ports/mail/qmail-tls/work/stage/var/qmail/man/man1 install -m 444 /usr/ports/mail/qmail-tls/work/netqmail-1.06/bouncesaying.1 /usr/ports/mail/qmail-tls/work/stage/var/qmail/man/man1 install -m 444 /usr/ports/mail/qmail-tls/work/netqmail-1.06/except.1 /usr/ports/mail/qmail-tls/work/stage/var/qmail/man/man1 install -m 444 /usr/ports/mail/qmail-tls/work/netqmail-1.06/maildirmake.1 /usr/ports/mail/qmail-tls/work/stage/var/qmail/man/man1 install -m 444 /usr/ports/mail/qmail-tls/work/netqmail-1.06/maildir2mbox.1 /usr/ports/mail/qmail-tls/work/stage/var/qmail/man/man1 install -m 444 /usr/ports/mail/qmail-tls/work/netqmail-1.06/maildirwatch.1 /usr/ports/mail/qmail-tls/work/stage/var/qmail/man/man1 install -m 444 /usr/ports/mail/qmail-tls/work/netqmail-1.06/mailsubj.1 /usr/ports/mail/qmail-tls/work/stage/var/qmail/man/man1 install -m 444 /usr/ports/mail/qmail-tls/work/netqmail-1.06/qreceipt.1 /usr/ports/mail/qmail-tls/work/stage/var/qmail/man/man1 install -m 444 /usr/ports/mail/qmail-tls/work/netqmail-1.06/qbiff.1 /usr/ports/mail/qmail-tls/work/stage/var/qmail/man/man1 install -m 444 /usr/ports/mail/qmail-tls/work/netqmail-1.06/preline.1 /usr/ports/mail/qmail-tls/work/stage/var/qmail/man/man1 install -m 444 /usr/ports/mail/qmail-tls/work/netqmail-1.06/tcp-env.1 /usr/ports/mail/qmail-tls/work/stage/var/qmail/man/man1 install -m 444 /usr/ports/mail/qmail-tls/work/netqmail-1.06/addresses.5 /usr/ports/mail/qmail-tls/work/stage/var/qmail/man/man5 install -m 444 /usr/ports/mail/qmail-tls/work/netqmail-1.06/envelopes.5 /usr/ports/mail/qmail-tls/work/stage/var/qmail/man/man5 install -m 444 /usr/ports/mail/qmail-tls/work/netqmail-1.06/maildir.5 /usr/ports/mail/qmail-tls/work/stage/var/qmail/man/man5 install -m 444 /usr/ports/mail/qmail-tls/work/netqmail-1.06/mbox.5 /usr/ports/mail/qmail-tls/work/stage/var/qmail/man/man5 install -m 444 /usr/ports/mail/qmail-tls/work/netqmail-1.06/dot-qmail.5 /usr/ports/mail/qmail-tls/work/stage/var/qmail/man/man5 install -m 444 /usr/ports/mail/qmail-tls/work/netqmail-1.06/qmail-control.5 /usr/ports/mail/qmail-tls/work/stage/var/qmail/man/man5 install -m 444 /usr/ports/mail/qmail-tls/work/netqmail-1.06/qmail-header.5 /usr/ports/mail/qmail-tls/work/stage/var/qmail/man/man5 install -m 444 /usr/ports/mail/qmail-tls/work/netqmail-1.06/qmail-log.5 /usr/ports/mail/qmail-tls/work/stage/var/qmail/man/man5 install -m 444 /usr/ports/mail/qmail-tls/work/netqmail-1.06/qmail-users.5 /usr/ports/mail/qmail-tls/work/stage/var/qmail/man/man5 install -m 444 /usr/ports/mail/qmail-tls/work/netqmail-1.06/tcp-environ.5 /usr/ports/mail/qmail-tls/work/stage/var/qmail/man/man5 install -m 444 /usr/ports/mail/qmail-tls/work/netqmail-1.06/forgeries.7 /usr/ports/mail/qmail-tls/work/stage/var/qmail/man/man7 install -m 444 /usr/ports/mail/qmail-tls/work/netqmail-1.06/qmail-limits.7 /usr/ports/mail/qmail-tls/work/stage/var/qmail/man/man7 install -m 444 /usr/ports/mail/qmail-tls/work/netqmail-1.06/qmail.7 /usr/ports/mail/qmail-tls/work/stage/var/qmail/man/man7 install -m 444 /usr/ports/mail/qmail-tls/work/netqmail-1.06/qmail-local.8 /usr/ports/mail/qmail-tls/work/stage/var/qmail/man/man8 install -m 444 /usr/ports/mail/qmail-tls/work/netqmail-1.06/qmail-lspawn.8 /usr/ports/mail/qmail-tls/work/stage/var/qmail/man/man8 install -m 444 /usr/ports/mail/qmail-tls/work/netqmail-1.06/qmail-getpw.8 /usr/ports/mail/qmail-tls/work/stage/var/qmail/man/man8 install -m 444 /usr/ports/mail/qmail-tls/work/netqmail-1.06/qmail-remote.8 /usr/ports/mail/qmail-tls/work/stage/var/qmail/man/man8 install -m 444 /usr/ports/mail/qmail-tls/work/netqmail-1.06/qmail-rspawn.8 /usr/ports/mail/qmail-tls/work/stage/var/qmail/man/man8 install -m 444 /usr/ports/mail/qmail-tls/work/netqmail-1.06/qmail-clean.8 /usr/ports/mail/qmail-tls/work/stage/var/qmail/man/man8 install -m 444 /usr/ports/mail/qmail-tls/work/netqmail-1.06/qmail-send.8 /usr/ports/mail/qmail-tls/work/stage/var/qmail/man/man8 install -m 444 /usr/ports/mail/qmail-tls/work/netqmail-1.06/qmail-start.8 /usr/ports/mail/qmail-tls/work/stage/var/qmail/man/man8 install -m 444 /usr/ports/mail/qmail-tls/work/netqmail-1.06/splogger.8 /usr/ports/mail/qmail-tls/work/stage/var/qmail/man/man8 install -m 444 /usr/ports/mail/qmail-tls/work/netqmail-1.06/qmail-queue.8 /usr/ports/mail/qmail-tls/work/stage/var/qmail/man/man8 install -m 444 /usr/ports/mail/qmail-tls/work/netqmail-1.06/qmail-inject.8 /usr/ports/mail/qmail-tls/work/stage/var/qmail/man/man8 install -m 444 /usr/ports/mail/qmail-tls/work/netqmail-1.06/qmail-showctl.8 /usr/ports/mail/qmail-tls/work/stage/var/qmail/man/man8 install -m 444 /usr/ports/mail/qmail-tls/work/netqmail-1.06/qmail-newmrh.8 /usr/ports/mail/qmail-tls/work/stage/var/qmail/man/man8 install -m 444 /usr/ports/mail/qmail-tls/work/netqmail-1.06/qmail-newu.8 /usr/ports/mail/qmail-tls/work/stage/var/qmail/man/man8 install -m 444 /usr/ports/mail/qmail-tls/work/netqmail-1.06/qmail-pw2u.8 /usr/ports/mail/qmail-tls/work/stage/var/qmail/man/man8 install -m 444 /usr/ports/mail/qmail-tls/work/netqmail-1.06/qmail-qread.8 /usr/ports/mail/qmail-tls/work/stage/var/qmail/man/man8 install -m 444 /usr/ports/mail/qmail-tls/work/netqmail-1.06/qmail-qstat.8 /usr/ports/mail/qmail-tls/work/stage/var/qmail/man/man8 install -m 444 /usr/ports/mail/qmail-tls/work/netqmail-1.06/qmail-tcpok.8 /usr/ports/mail/qmail-tls/work/stage/var/qmail/man/man8 install -m 444 /usr/ports/mail/qmail-tls/work/netqmail-1.06/qmail-tcpto.8 /usr/ports/mail/qmail-tls/work/stage/var/qmail/man/man8 install -m 444 /usr/ports/mail/qmail-tls/work/netqmail-1.06/qmail-pop3d.8 /usr/ports/mail/qmail-tls/work/stage/var/qmail/man/man8 install -m 444 /usr/ports/mail/qmail-tls/work/netqmail-1.06/qmail-popup.8 /usr/ports/mail/qmail-tls/work/stage/var/qmail/man/man8 install -m 444 /usr/ports/mail/qmail-tls/work/netqmail-1.06/qmail-qmqpc.8 /usr/ports/mail/qmail-tls/work/stage/var/qmail/man/man8 install -m 444 /usr/ports/mail/qmail-tls/work/netqmail-1.06/qmail-qmqpd.8 /usr/ports/mail/qmail-tls/work/stage/var/qmail/man/man8 install -m 444 /usr/ports/mail/qmail-tls/work/netqmail-1.06/qmail-qmtpd.8 /usr/ports/mail/qmail-tls/work/stage/var/qmail/man/man8 install -m 444 /usr/ports/mail/qmail-tls/work/netqmail-1.06/qmail-smtpd.8 /usr/ports/mail/qmail-tls/work/stage/var/qmail/man/man8 install -m 444 /usr/ports/mail/qmail-tls/work/netqmail-1.06/qmail-command.8 /usr/ports/mail/qmail-tls/work/stage/var/qmail/man/man8 install -m 0644 /usr/ports/mail/qmail-tls/work/netqmail-1.06/BLURB /usr/ports/mail/qmail-tls/work/stage/var/qmail/doc install -m 0644 /usr/ports/mail/qmail-tls/work/netqmail-1.06/BLURB2 /usr/ports/mail/qmail-tls/work/stage/var/qmail/doc install -m 0644 /usr/ports/mail/qmail-tls/work/netqmail-1.06/BLURB3 /usr/ports/mail/qmail-tls/work/stage/var/qmail/doc install -m 0644 /usr/ports/mail/qmail-tls/work/netqmail-1.06/BLURB4 /usr/ports/mail/qmail-tls/work/stage/var/qmail/doc install -m 0644 /usr/ports/mail/qmail-tls/work/netqmail-1.06/INTERNALS /usr/ports/mail/qmail-tls/work/stage/var/qmail/doc install -m 0644 /usr/ports/mail/qmail-tls/work/netqmail-1.06/SECURITY /usr/ports/mail/qmail-tls/work/stage/var/qmail/doc install -m 0644 /usr/ports/mail/qmail-tls/work/netqmail-1.06/THOUGHTS /usr/ports/mail/qmail-tls/work/stage/var/qmail/doc install -m 0644 /usr/ports/mail/qmail-tls/work/netqmail-1.06/FAQ /usr/ports/mail/qmail-tls/work/stage/var/qmail/doc install -m 0644 /usr/ports/mail/qmail-tls/work/netqmail-1.06/UPGRADE /usr/ports/mail/qmail-tls/work/stage/var/qmail/doc install -m 0644 /usr/ports/mail/qmail-tls/work/netqmail-1.06/SENDMAIL /usr/ports/mail/qmail-tls/work/stage/var/qmail/doc install -m 0644 /usr/ports/mail/qmail-tls/work/netqmail-1.06/INSTALL /usr/ports/mail/qmail-tls/work/stage/var/qmail/doc install -m 0644 /usr/ports/mail/qmail-tls/work/netqmail-1.06/INSTALL.alias /usr/ports/mail/qmail-tls/work/stage/var/qmail/doc install -m 0644 /usr/ports/mail/qmail-tls/work/netqmail-1.06/INSTALL.ctl /usr/ports/mail/qmail-tls/work/stage/var/qmail/doc install -m 0644 /usr/ports/mail/qmail-tls/work/netqmail-1.06/INSTALL.ids /usr/ports/mail/qmail-tls/work/stage/var/qmail/doc install -m 0644 /usr/ports/mail/qmail-tls/work/netqmail-1.06/INSTALL.maildir /usr/ports/mail/qmail-tls/work/stage/var/qmail/doc install -m 0644 /usr/ports/mail/qmail-tls/work/netqmail-1.06/INSTALL.mbox /usr/ports/mail/qmail-tls/work/stage/var/qmail/doc install -m 0644 /usr/ports/mail/qmail-tls/work/netqmail-1.06/INSTALL.vsm /usr/ports/mail/qmail-tls/work/stage/var/qmail/doc install -m 0644 /usr/ports/mail/qmail-tls/work/netqmail-1.06/TEST.deliver /usr/ports/mail/qmail-tls/work/stage/var/qmail/doc install -m 0644 /usr/ports/mail/qmail-tls/work/netqmail-1.06/TEST.receive /usr/ports/mail/qmail-tls/work/stage/var/qmail/doc install -m 0644 /usr/ports/mail/qmail-tls/work/netqmail-1.06/REMOVE.sendmail /usr/ports/mail/qmail-tls/work/stage/var/qmail/doc install -m 0644 /usr/ports/mail/qmail-tls/work/netqmail-1.06/REMOVE.binmail /usr/ports/mail/qmail-tls/work/stage/var/qmail/doc install -m 0644 /usr/ports/mail/qmail-tls/work/netqmail-1.06/PIC.local2alias /usr/ports/mail/qmail-tls/work/stage/var/qmail/doc install -m 0644 /usr/ports/mail/qmail-tls/work/netqmail-1.06/PIC.local2ext /usr/ports/mail/qmail-tls/work/stage/var/qmail/doc install -m 0644 /usr/ports/mail/qmail-tls/work/netqmail-1.06/PIC.local2local /usr/ports/mail/qmail-tls/work/stage/var/qmail/doc install -m 0644 /usr/ports/mail/qmail-tls/work/netqmail-1.06/PIC.local2rem /usr/ports/mail/qmail-tls/work/stage/var/qmail/doc install -m 0644 /usr/ports/mail/qmail-tls/work/netqmail-1.06/PIC.local2virt /usr/ports/mail/qmail-tls/work/stage/var/qmail/doc install -m 0644 /usr/ports/mail/qmail-tls/work/netqmail-1.06/PIC.nullclient /usr/ports/mail/qmail-tls/work/stage/var/qmail/doc install -m 0644 /usr/ports/mail/qmail-tls/work/netqmail-1.06/PIC.relaybad /usr/ports/mail/qmail-tls/work/stage/var/qmail/doc install -m 0644 /usr/ports/mail/qmail-tls/work/netqmail-1.06/PIC.relaygood /usr/ports/mail/qmail-tls/work/stage/var/qmail/doc install -m 0644 /usr/ports/mail/qmail-tls/work/netqmail-1.06/PIC.rem2local /usr/ports/mail/qmail-tls/work/stage/var/qmail/doc install -m 0644 /usr/ports/mail/qmail-tls/work/mailer.conf.sample /usr/ports/mail/qmail-tls/work/stage/var/qmail/doc install -m 0644 /usr/ports/mail/qmail-tls/work/TLS.readme /usr/ports/mail/qmail-tls/work/stage/var/qmail/doc install -m 555 /usr/ports/mail/qmail-tls/../qmail/files/mkaliasdir /usr/ports/mail/qmail-tls/work/stage/var/qmail/scripts install -m 555 /usr/ports/mail/qmail-tls/work/enable-qmail /usr/ports/mail/qmail-tls/work/stage/var/qmail/scripts ============================================= ATTENTION Add the following line to your /etc/make.conf QMAIL_SLAVEPORT=tls ============================================= install -m 0644 /usr/ports/mail/qmail-tls/work/qmail.conf /usr/ports/mail/qmail-tls/work/stage/usr/local/etc/man.d/qmail.conf ===> Fixing plist for /var/qmail ownership /bin/rm -f -r /usr/ports/mail/qmail-tls/work/stage/var/qmail/queue/ ====> Compressing man pages (compress-man)
# make install
===> Installing for netqmail-tls-1.06.20200107_4
===> Checking if netqmail-tls is already installed
===> Registering installation for netqmail-tls-1.06.20200107_4
pkg-static: Warning: @unexec is deprecated, please use @[pre|post]unexec
pkg-static: Warning: @exec is deprecated, please use @[pre|post][un]exec
Installing netqmail-tls-1.06.20200107_4...
===> Creating groups.
Using existing group 'qmail'.
Using existing group 'qnofiles'.
===> Creating users
Using existing user 'alias'.
===> Creating homedir(s)
Using existing user 'qmaild'.
===> Creating homedir(s)
Using existing user 'qmaill'.
===> Creating homedir(s)
Using existing user 'qmailp'.
===> Creating homedir(s)
Using existing user 'qmailq'.
===> Creating homedir(s)
Using existing user 'qmailr'.
===> Creating homedir(s)
Using existing user 'qmails'.
===> Creating homedir(s)
Your hostname is ns3.te-clan.ch.
hard error
Sorry, I couldn't find your host's canonical name in DNS.
You will have to set up control/me yourself.
ATTENTION:
Do not forget to read /var/qmail/doc/TLS.readme. After all,
this is NOT our old stock qmail.
You can enable qmail as your default mailer executing:
> /var/qmail/scripts/enable-qmail
==> As you need to provide a working certificate in /var/qmail/control/cert.pem :
# makes a self-signed certificate
3) do "make certificate"
# makes a certificate request
4) do "make certificate-req"
===> SECURITY REPORT:
This port has installed the following binaries which execute with
increased privileges.
/var/qmail/bin/qmail-queue
If there are vulnerabilities in these programs there may be a security
risk to the system. FreeBSD makes no guarantee about the security of
ports included in the Ports Collection. Please type 'make deinstall'
to deinstall the port if this is a concern.
For more information, and contact details about the security
status of this software, see the following webpage:
http://inoa.net/qmail-tls/